The Transform Technology Summits start October 13th with Low-Code/No Code: Enabling Enterprise Agility. Register now!
(adsbygoogle = window.adsbygoogle || []).push({});
The last decade’s growing interest in deep learning was triggered by the proven capacity of neural networks in computer vision tasks. If you train a neural network with enough labeled photos of cats and dogs, it will be able to find recurring patterns in each category and classify unseen images with decent accuracy.
What else can you do with an image classifier?
In 2019, a group of cybersecurity researchers wondered if they could treat security threat detection as an image classification problem. Their intuition proved to be well-placed, and they were able to create a machine learning model that could detect malware based on images created from the content of application files. A year later, the same technique was used to develop a machine learning system that detects phishing websites.
The combination of binary visualization and machine learning is a powerful technique that can provide new solutions to old problems. It is showing promise in cybersecurity, but it could also be applied to other domains.
Detecting malware with deep learning
The traditional way to detect malware is to search files for known signatures of malicious payloads. Malware detectors maintain a database of virus definitions which include opcode sequences or code snippets, and they search new files for the presence of these signatures. Unfortunately, malware developers can easily circumvent such detection methods using different techniques such as obfuscating their code or using polymorphism techniques to mutate their code at runtime.
Dynamic analysis tools try to detect malicious behavior during runtime, but they are slow and require the setup of a sandbox environment to test suspicious programs.
In recent years, researchers have also tried a range of machine learning techniques to detect malware. These ML models have managed to make progress on some of the challenges of malware detection, including code obfuscation. But they present new challenges, including the need to learn too many features and a virtual environment to analyze the target samples.
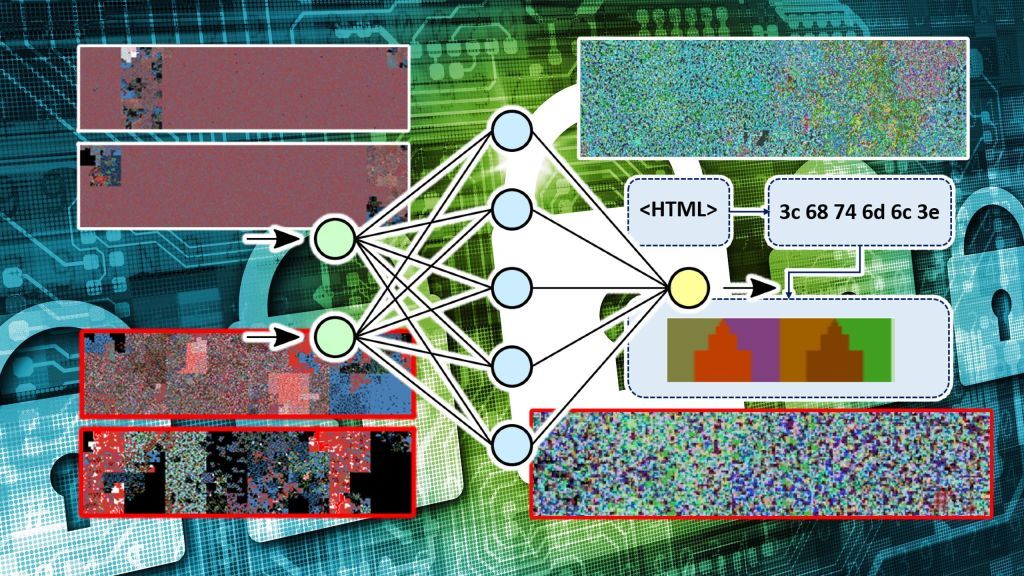
Binary visualization can redefine malware detection by turning it into a computer vision problem. In this methodology, files are run through algorithms that transform binary and ASCII values to color codes.
In a paper published in 2019, researchers at the University of Plymouth and the University of Peloponnese showed that when benign and malicious files were visualized using this method, new patterns emerge that separate malicious and safe files. These differences would have gone unnoticed using classic malware detection methods.
artificial neural network to tell the difference between malicious and safe files. The researchers created a dataset of visualized binary files that included both benign and malign files. The dataset contained a variety of malicious payloads (viruses, worms, trojans, rootkits, etc.) and file types (.exe, .doc, .pdf, .txt, etc.).
The researchers then used the images to train a classifier neural network. The architecture they used is the self-organizing incremental neural network (SOINN), which is fast and is especially good at dealing with noisy data. They also used an image preprocessing technique to shrink the binary images into 1,024-dimension feature vectors, which makes it much easier and compute-efficient to learn patterns in the input data.
ransomware attacks. The researchers suggested that the model’s performance can be improved if it is adjusted to take the filetype as one of its learning dimensions. Overall, the algorithm achieved an average detection rate of around 74 percent.
Detecting phishing websites with deep learning
Phishing attacks are becoming a growing problem for organizations and individuals. Many phishing attacks trick the victims into clicking on a link to a malicious website that poses as a legitimate service, where they end up entering sensitive information such as credentials or financial information.
Traditional approaches for detecting phishing websites revolve around blacklisting malicious domains or whitelisting safe domains. The former method misses new phishing websites until someone falls victim, and the latter is too restrictive and requires extensive efforts to provide access to all safe domains.
Other detection methods rely on heuristics. These methods are more accurate than blacklists, but they still fall short of providing optimal detection.
In 2020, a group of researchers at the University of Plymouth and the University of Portsmouth used binary visualization and deep learning to develop a novel method for detecting phishing websites.
The technique uses binary visualization libraries to transform website markup and source code into color values.
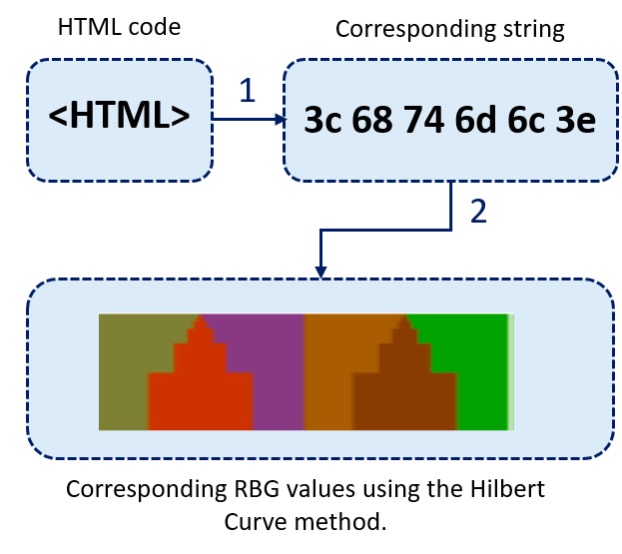
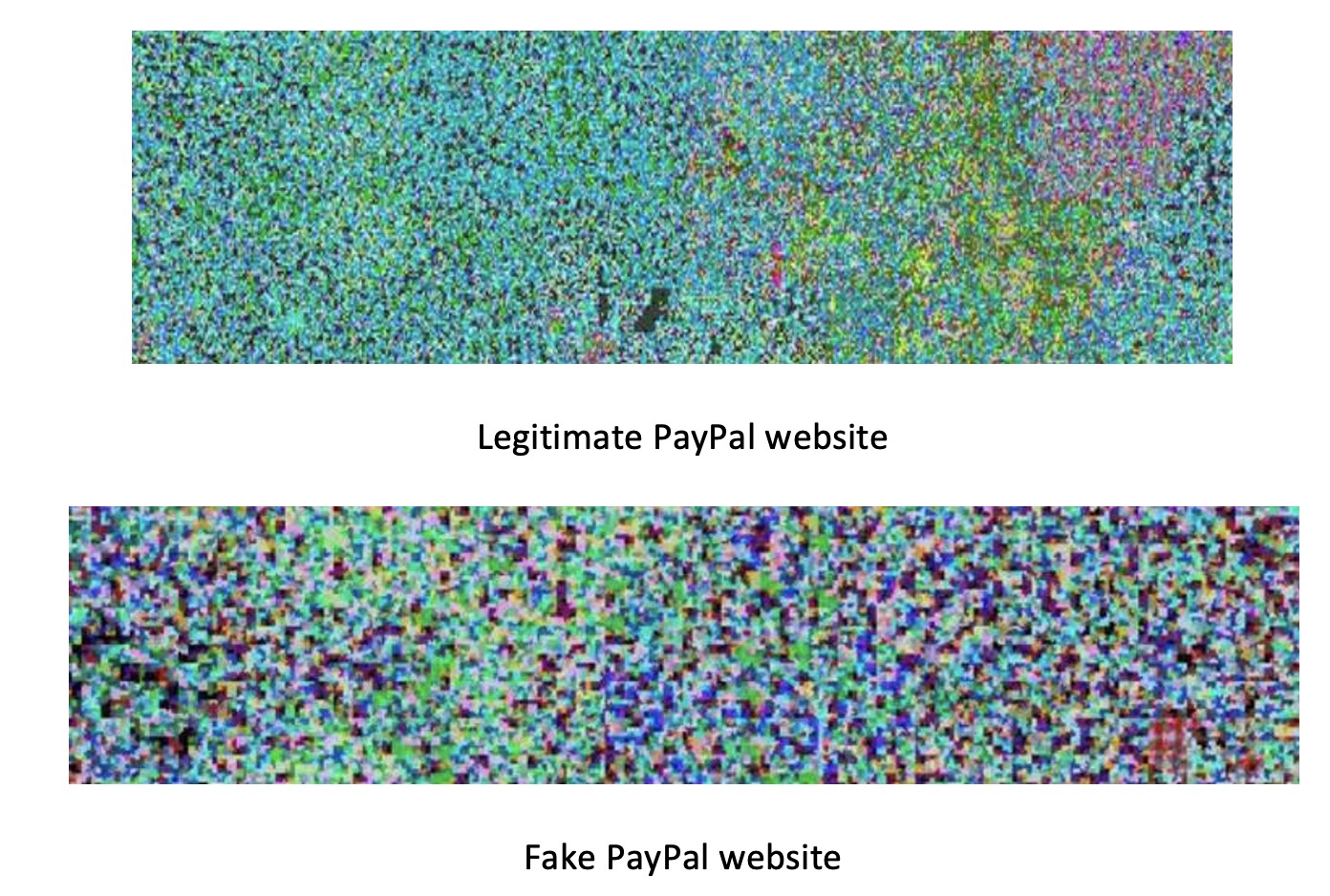
As is the case with benign and malign application files, when visualizing websites, unique patterns emerge that separate safe and malicious websites. The researchers write, “The legitimate site has a more detailed RGB value because it would be constructed from additional characters sourced from licenses, hyperlinks, and detailed data entry forms. Whereas the phishing counterpart would generally contain a single or no CSS reference, multiple images rather than forms and a single login form with no security scripts. This would create a smaller data input string when scraped.”
The example below shows the visual representation of the code of the legitimate PayPal login compared to a fake phishing PayPal website.
The researchers created a dataset of images representing the code of legitimate and malicious websites and used it to train a classification machine learning model.
The architecture they used is MobileNet, a lightweight convolutional neural network (CNN) that is optimized to run on user devices instead of high-capacity cloud servers. CNNs are especially suited for computer vision tasks including image classification and object detection.
Once the model is trained, it is plugged into a phishing detection tool. When the user stumbles on a new website, it first checks whether the URL is included in its database of malicious domains. If it’s a new domain, then it is transformed through the visualization algorithm and run through the neural network to check if it has the patterns of malicious websites. This two-step architecture makes sure the system uses the speed of blacklist databases and the smart detection of the neural network–based phishing detection technique.
The researchers’ experiments showed that the technique could detect phishing websites with 94 percent accuracy. “Using visual representation techniques allows to obtain an insight into the structural differences between legitimate and phishing web pages. From our initial experimental results, the method seems promising and being able to fast detection of phishing attacker with high accuracy. Moreover, the method learns from the misclassifications and improves its efficiency,” the researchers wrote.
IoT networks.
As machine learning continues to make progress, it will provide scientists new tools to address cybersecurity challenges. Binary visualization shows that with enough creativity and rigor, we can find novel solutions to old problems.
This story originally appeared on Bdtechtalks.com. Copyright 2021
VentureBeat
VentureBeat’s mission is to be a digital town square for technical decision-makers to gain knowledge about transformative technology and transact.
Our site delivers essential information on data technologies and strategies to guide you as you lead your organizations. We invite you to become a member of our community, to access:
- up-to-date information on the subjects of interest to you
- our newsletters
- gated thought-leader content and discounted access to our prized events, such as Transform 2021: Learn More
- networking features, and more
Leave a Reply Cancel reply
document.addEventListener(‘DOMContentLoaded’,function(){var commentForms=document.getElementsByClassName(‘jetpack_remote_comment’);for(var i=0;i<commentForms.length;i++){commentForms[i].allowTransparency=false;commentForms.scrolling='no';}}); <!–
(adsbygoogle = window.adsbygoogle || []).push({});
Zoom’s new collaboration features for hybrid work will be rolling out throughout the remainder of this year.
https://blog.zoom.us/zoom-platform-enhancements-zoomtopia-2021/
Today’s Best Tech Deals
Picked by PCWorld’s Editors
Top Deals On Great Products
Picked by Techconnect’s Editors
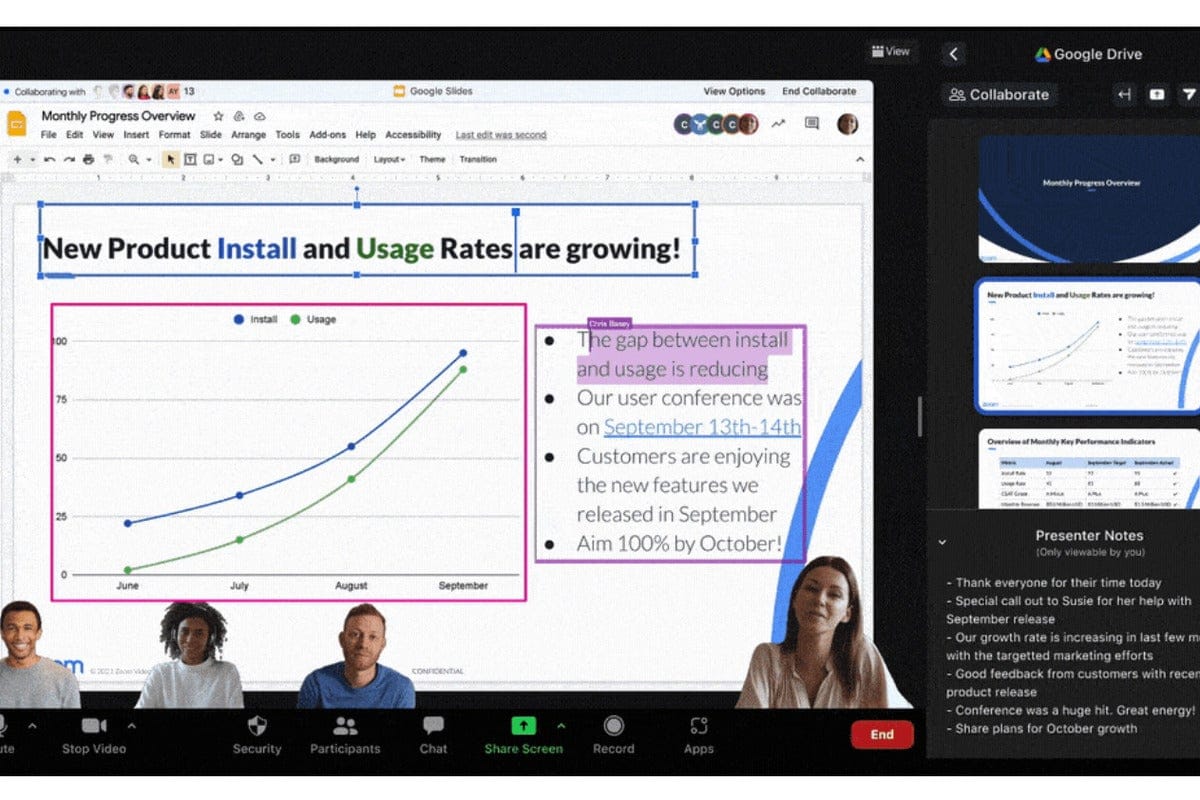
Remember when Zoom was just our pandemic video-chat app? Now the service is adding collaboration features of all stripes, including translation, whiteboarding, and even voice mail, while challenging established players like Microsoft Teams and Slack.
Zoom kicked off its Zoomtopia user conference by announcing a ton of new features, par for the course during the whirlwind days of the pandemic when Google, Microsoft, Zoom, and others competed for users. Now, as the world moves into a hybrid work environment, Zoom is trying to capture a greater percentage of both in-person and remote workers. (Zoom hedged its bets by saying that these are “future potential projects.”)
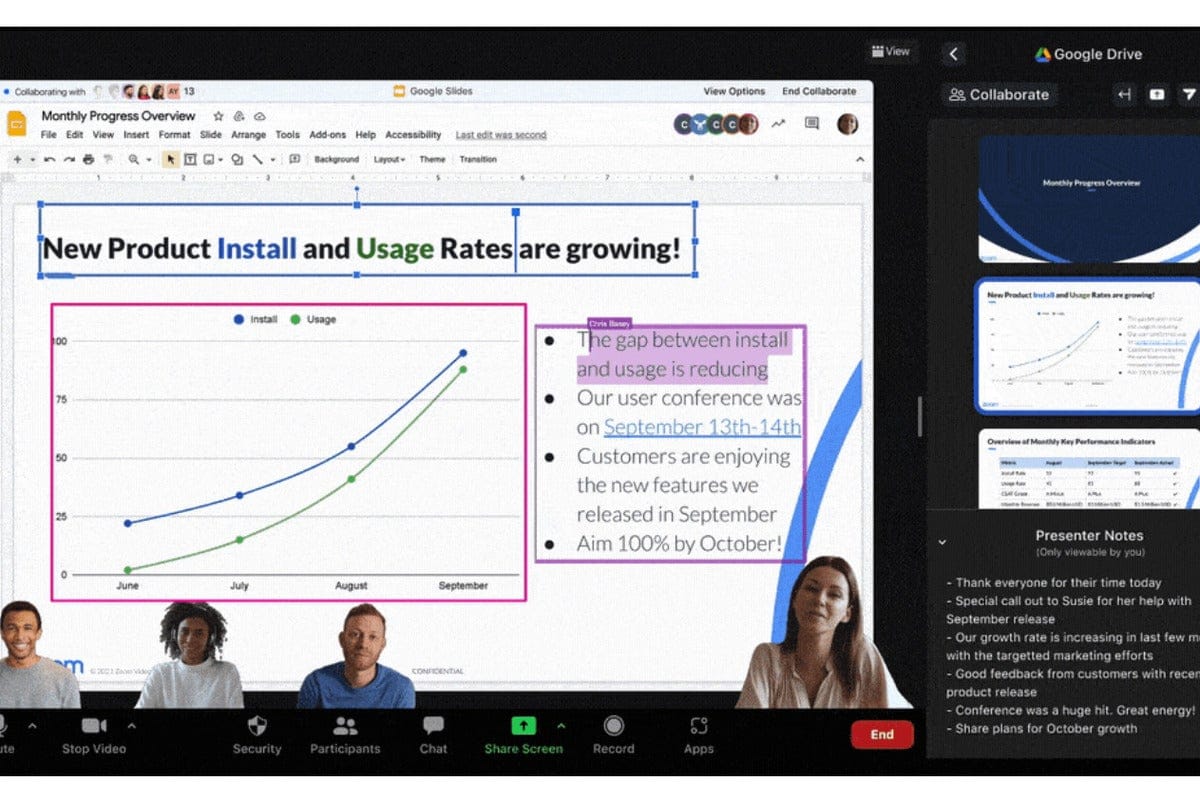
The most obvious changes, however, are in how Zoom is expanding its chat capabilities, providing an experience that looks quite a bit like Slack.
 Zoom
Zoom Zoom Chat looks quite a bit like the Slack interface.
This is part of what Zoom calls “continuous collaboration,” where you’ll be able to chat about a task, exchange documents, drop into a video call, and even share automated video transcriptions and translations—a feature that Microsoft Teams helped pioneer, and now Zoom is adding, too. Zoom also said that it’s partnering with Microsoft SharePoint and Box to allow you to share files. Finally, Chat is adding a “Huddle View” for closer team collaboration.
Zoom is also adding a virtual whiteboarding solution, another type of collaborative workspace that Monday.com recently added, and that also appears in Google Meet and other collaborative workspace applications. Zoom’s whiteboard, which the company says is “anticipated later this year,” will exist online in 2D space, but will also be part of the Oculus Horizons Workrooms initiative that Facebook is building in VR. Do you need to chat in the waiting room while waiting for a meeting? That feature’s coming later this year, too.
 https://blog.zoom.us/zoom-platform-enhancements-zoomtopia-2021/
https://blog.zoom.us/zoom-platform-enhancements-zoomtopia-2021/Zoom’s new whiteboarding solution.
In July, Zoom announced Zoom Apps, the capability to add apps directly to your Zoom experience—again, a capability that Microsoft Teams has announced previously. On Monday, Zoom said that a sub-category of new, “immersive” apps will allow you to embed yourself via Zoom directly into another app—for example, you’ll be able to put a small video feed of yourself in the corner of a Google Docs presentation. We’ve seen this capability in apps like mmhmm and others, but it’s coming to Zoom, now, too.
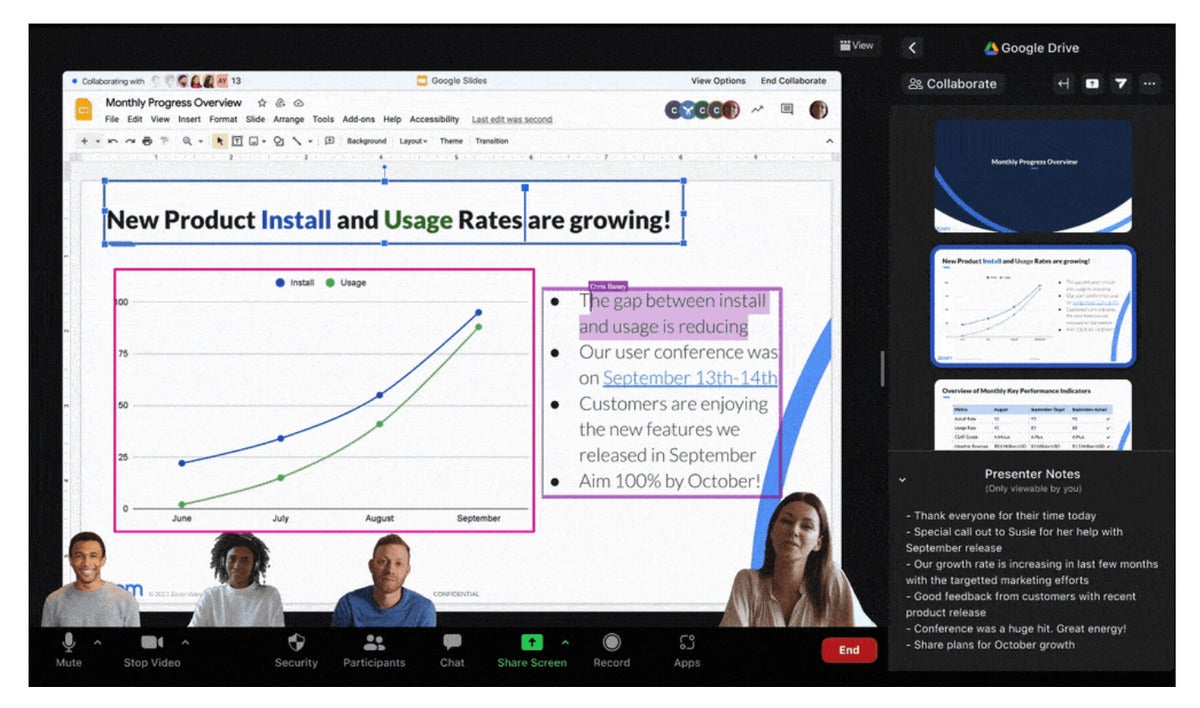 https://blog.zoom.us/zoom-platform-enhancements-zoomtopia-2021/
https://blog.zoom.us/zoom-platform-enhancements-zoomtopia-2021/Placing a streamed video of yourself into a presentation seems like a more common feature thse days, and Zoom is jumping in.
Finally, Zoom is adding a Zoom widget for your desktop. It looks like the widget will simply offer an at-a-glance summary of your meeting calendar, with links to the Zoom call if necessary.
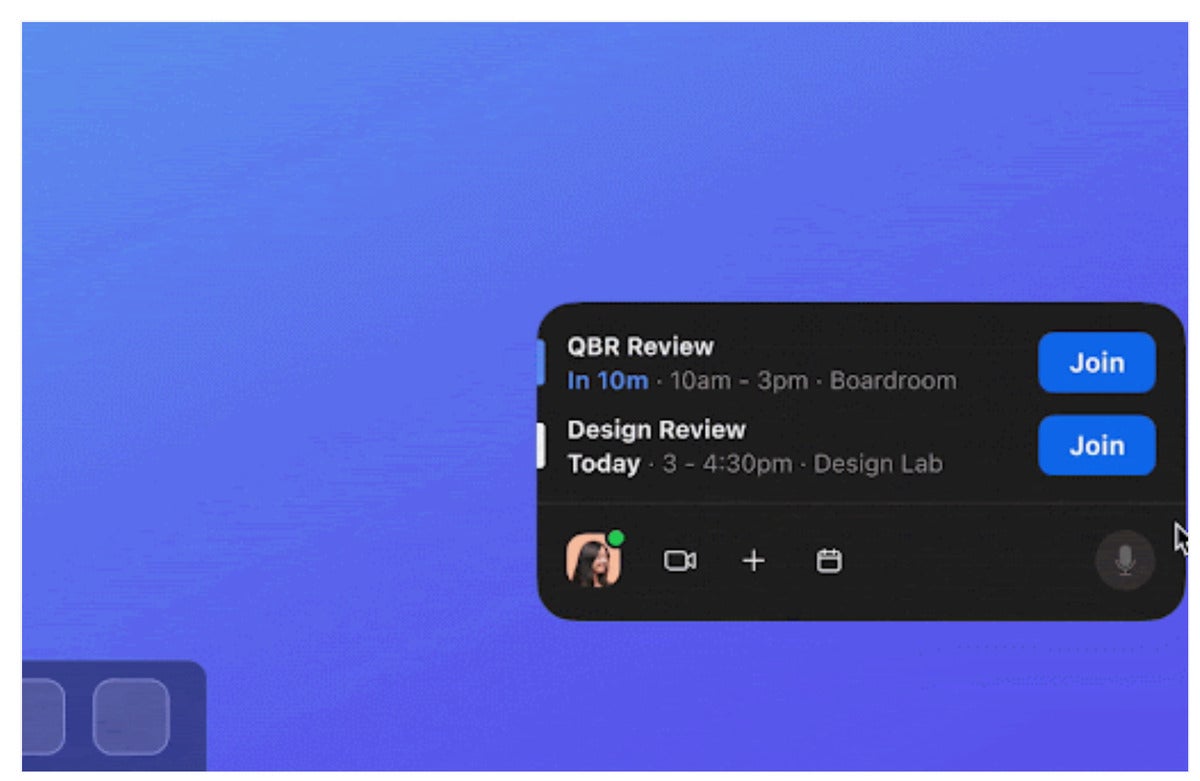 https://blog.zoom.us/zoom-platform-enhancements-zoomtopia-2021/
https://blog.zoom.us/zoom-platform-enhancements-zoomtopia-2021/The Zoom widget.
Zoom’s hybrid workspace plans include a new feature to “hot desk,” where you’ll be able to reserve a desk in a workplace with limited access during the pandemic. If you’re actually in the office, seated around a conference room, a new “Smart Gallery” feature will automatically take the panoramic view a webcam captures of the attendees and carve out AI-generated individual video feeds.
Zoom is also bringing with it one of the unfortunate legacies of the workspace: its dedicated Zoom phones will be adding voice mail, too.
Note: When you purchase something after clicking links in our articles, we may earn a small commission. Read our affiliate link policy for more details.
As PCWorld’s senior editor, Mark focuses on Microsoft news and chip technology, among other beats.
Tech
AMD Radeon Software can overclock your Ryzen CPU now, too

Published
15 hours ago
on
13/09/2021
By


(adsbygoogle = window.adsbygoogle || []).push({});
A virtual turbo button.

Gordon Mah Ung
Today’s Best Tech Deals
Picked by PCWorld’s Editors
Top Deals On Great Products
Picked by Techconnect’s Editors
The latest version of Radeon Software adds an unusual (and welcome) new twist: The ability to automatically overclock your Ryzen processor if you’re rocking an all-AMD gaming desktop. Yes, your GPU software can speed up your CPU now, too—and it can do it all with a single click.
The addition might not come as a surprise if you’ve been paying close attention to AMD’s behavior over the past year. Now that Ryzen bests Intel processors and Radeon graphics cards go blow-for-blow with Nvidia’s top GPUs, gamers can get no-compromises performance from an all-AMD rig for the first time in many years—and AMD has been working hard to strengthen the ties between the two product lineups. Smart Access Memory grants your Ryzen CPU full access to your Radeon GPU’s memory, while Smart Shift technology lets laptops with a Ryzen/Radeon combo intelligently shift more power to either component when it’s needed for faster performance. And earlier this year, AMD worked Ryzen performance monitoring into Radeon Software.
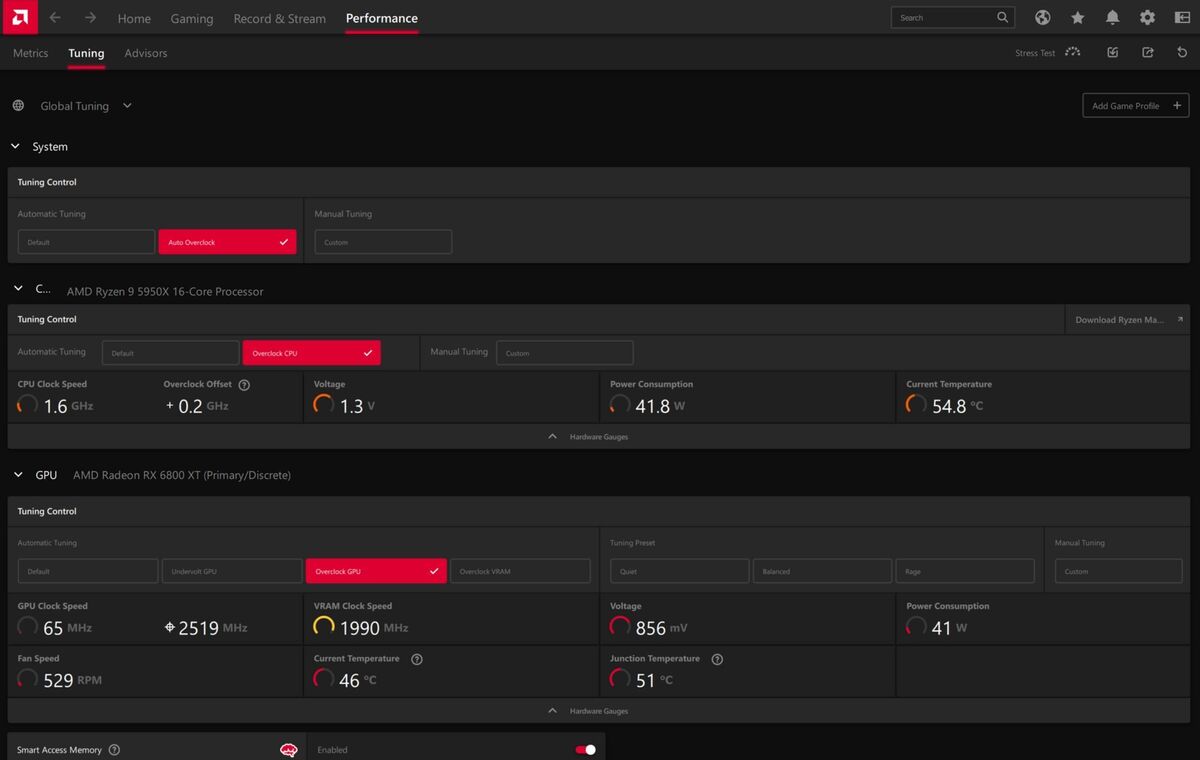 AMD
AMD The new auto-tuning controls in Radeon Software, complete with Ryzen CPU support.
The addition of Ryzen auto-overclocking in Radeon Software 21.9.1 continues the theme, and might just allow you to ditch AMD’s separate Ryzen Master tool if you’re running a Team Red graphics card. They’ll need to be newer hardware, though, as the feature currently only supports AMD’s latest Ryzen 5000 CPUs and Radeon RX 6000 GPUs.
AMD’s blog describes how to use the new tool:
To access this easy-to-use feature, open up Radeon Software using the hotkey ‘ALT’ + ‘R’, navigate to the ‘Performance’ tab found at the top of the window, and select ‘Tuning’ in the sub tab directly below it.
If you have the latest generation of AMD Ryzen and Radeon product installed on your system, a ‘Tuning Control’ section should appear for your system, allowing you to select ‘Auto Overclock’ to increase performance on both your processor and graphics card. We also have a new tuning section for CPUs, allowing you to overclock just your CPU.
When the feature is selected, the system will ask for a restart and once you are back in Windows, you will be good to go!
Groovy. Hardcore tinkerers will probably want to stick to third-party software that offers more granular controls, but for the vast majority of PC gamers, having a one-click “overclock everything” button for you all-AMD system should be a big bonus (assuming your cooling is up to snuff).
Beyond the newfound Ryzen synergy, Radeon Software 21.9.1 also adds official Windows 11 support and the ability for Radeon RX 5000-series GPUs to tap into Smart Access Memory. AMD also took the time to tout FidelityFX Super Resolution’s rapid uptake. The DLSS rival is now supported in 27 games, with Arkane’s awesome-looking Deathloop set to launch this week with native FSR support in place.
You can download these new drivers via AMD’s website or through your existing Radeon Software installation.
Note: When you purchase something after clicking links in our articles, we may earn a small commission. Read our affiliate link policy for more details.


(adsbygoogle = window.adsbygoogle || []).push({});
There are several easy ways to learn more about your system’s memory.

Corsair
Today’s Best Tech Deals
Picked by PCWorld’s Editors
Top Deals On Great Products
Picked by Techconnect’s Editors
For a very long time, the most common path to improving your PC’s performance has been through upgrading the RAM. RAM stands for “random access memory” and it’s effectively the component of your PC that is keeping track of what your computer is currently working on. When RAM is limited, your PC has to keep that current information stored somewhere else, which can dramatically slow down your workflow and load times. This is particularly notable in computationally heavy projects, such as video encoding and high-quality art creation.
Whether you’re looking to upgrade or you’re looking to harvest the RAM from one PC to use in another, it helps to know what kind of RAM your system is using. There are a handful of ways to figure that out!
In Windows 10
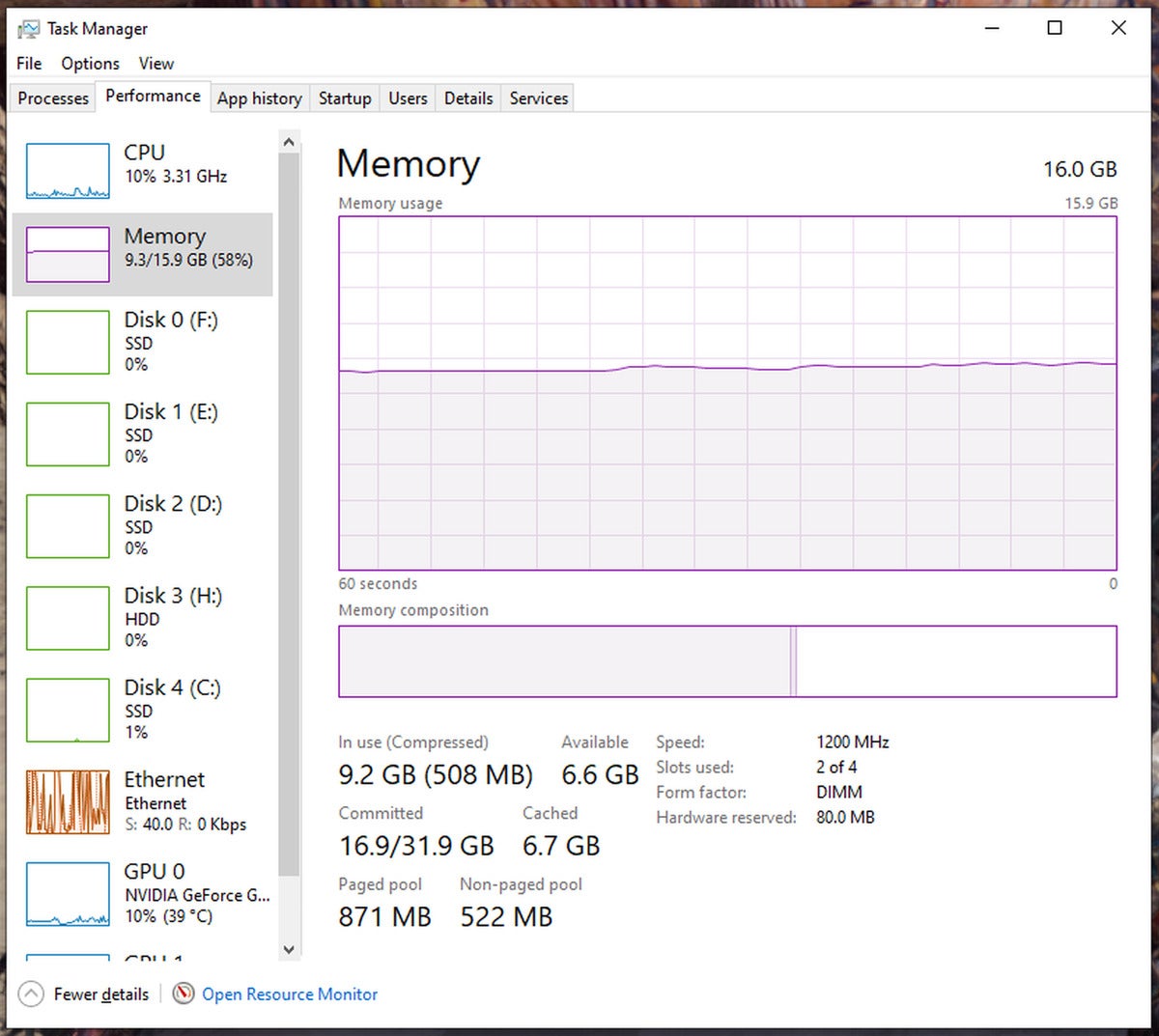
You can find basic information about your RAM through your system’s About page and through the Performance tab on your Task Manager.
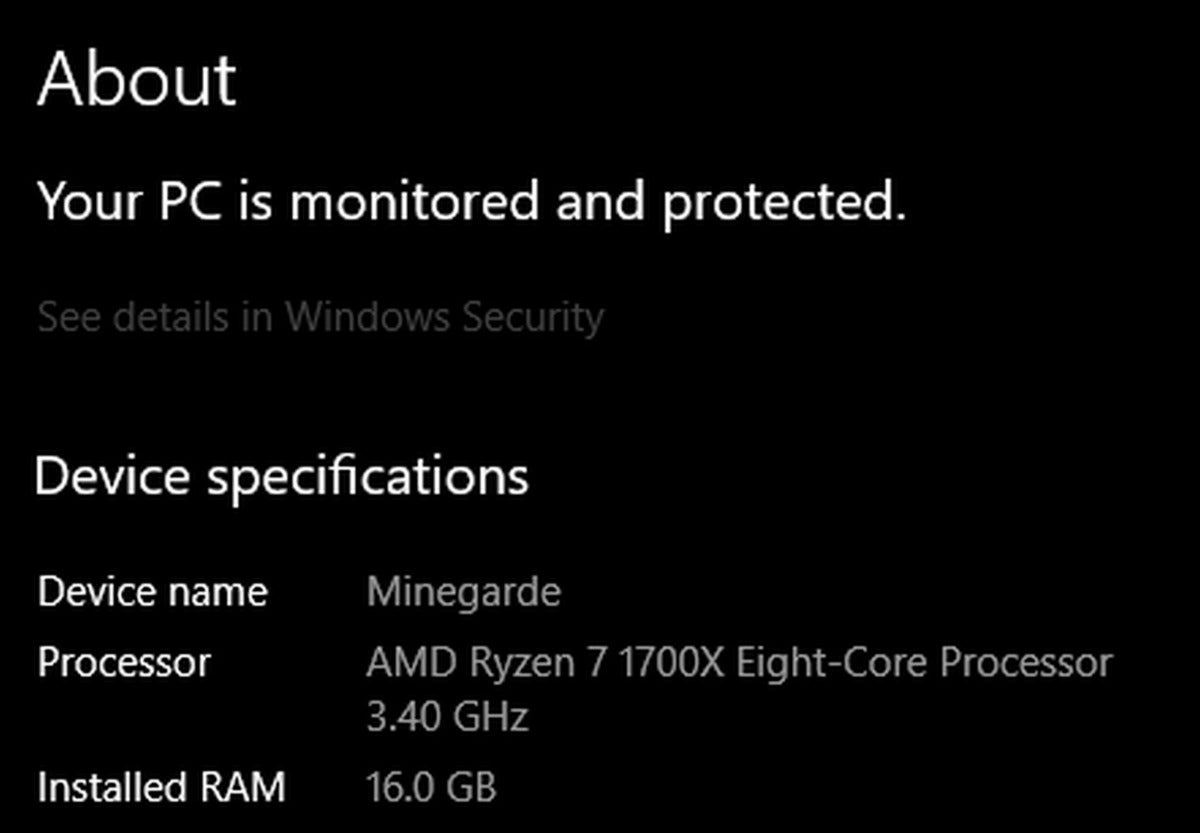 Kevin Casper/IDG
Kevin Casper/IDGHere are two simple methods to access the About page:
- Press the key combination Win + Pause/Break
- Type “About your PC” in the Windows Start menu search
 Kevin Casper/IDG
Kevin Casper/IDGTo access the Task Manager, here are three simple options:
- Press the key combination Ctrl + Shift + Escape
- Press the key combination Ctrl + Alt + Delete and select “Task Manager”
- Type “Task Manager” in the Windows Start menu search
These two methods will provide you with the most simplistic view of your PC’s RAM information, primarily showing how much RAM you currently have, along with some RAM speed information. If this isn’t enough information for what you’re looking to do, then you may want to check out the Windows Management Instrumentation command-line utility, or wmic.
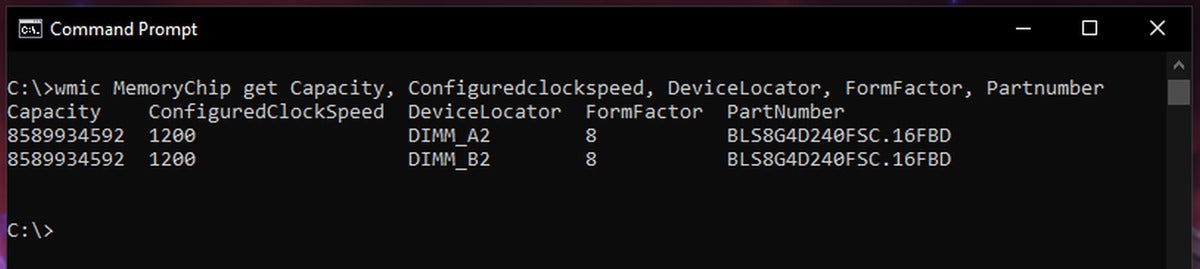 Kevin Casper/IDG
Kevin Casper/IDGIn order to use wmic, you need to open a Command Prompt window, which is quickly done by typing “cmd” into the Windows Start menu search. Once there, you can use a “wmic MemoryChip get” command to typically pull up the information you’re looking for.
You can find a comprehensive set of properties to include on your “wmic MemoryChip get” command here, but the following should cover the practical bases for most RAM identification needs:
wmic MemoryChip get MemoryType, Capacity, Speed, Configuredclockspeed, DeviceLocator, FormFactor, Manufacturer, Serialnumber, Partnumber
This will provide a table with the following information, if it’s available:
- MemoryType will report back a number that aligns to a particular “type” of RAM module. 20 means it’s DDR memory. DDR2 is 21. DDR3 is 24. DDR4 is 26. Sometimes, this may show a 0. If so, you’ll want to use “SMBIOSMemoryType” instead.
- Capacity will show the raw byte value of the RAM’s memory capacity, so something like 8,589,934,592 will be for an 8GB RAM module.
- Speed is the supported memory speed value that your RAM module indicates it can support, which is typically anywhere between 800 and 3200.
- Configuredclockspeed relates to the speed at which your RAM is currently configured to be running at.
- DeviceLocator will tell you which physical slot the RAM module is plugged into on your system’s motherboard.
- FormFactor is the physical shape type of the RAM module. This will typically be the number 8 for DIMM modules found on desktop PCs or the number 12 for laptops’ SODIMM forms.
- Manufacturer indicates an identified manufacturer of the RAM module. This may show up as Unknown sometimes.
- Serialnumber will give you the hardware serial number for that specific stick of RAM, which is typically only relevant when dealing with the manufacturer for troubleshooting purposes.
- Partnumber provides the manufacturer’s model number for that particular RAM module, which can be very useful with the help of a Google search to identify the RAM stick you have and whether or not you can buy it again.
Additional software options
Much of the above information is also available with the help of some third-party software, such as CPU-Z and Speccy.
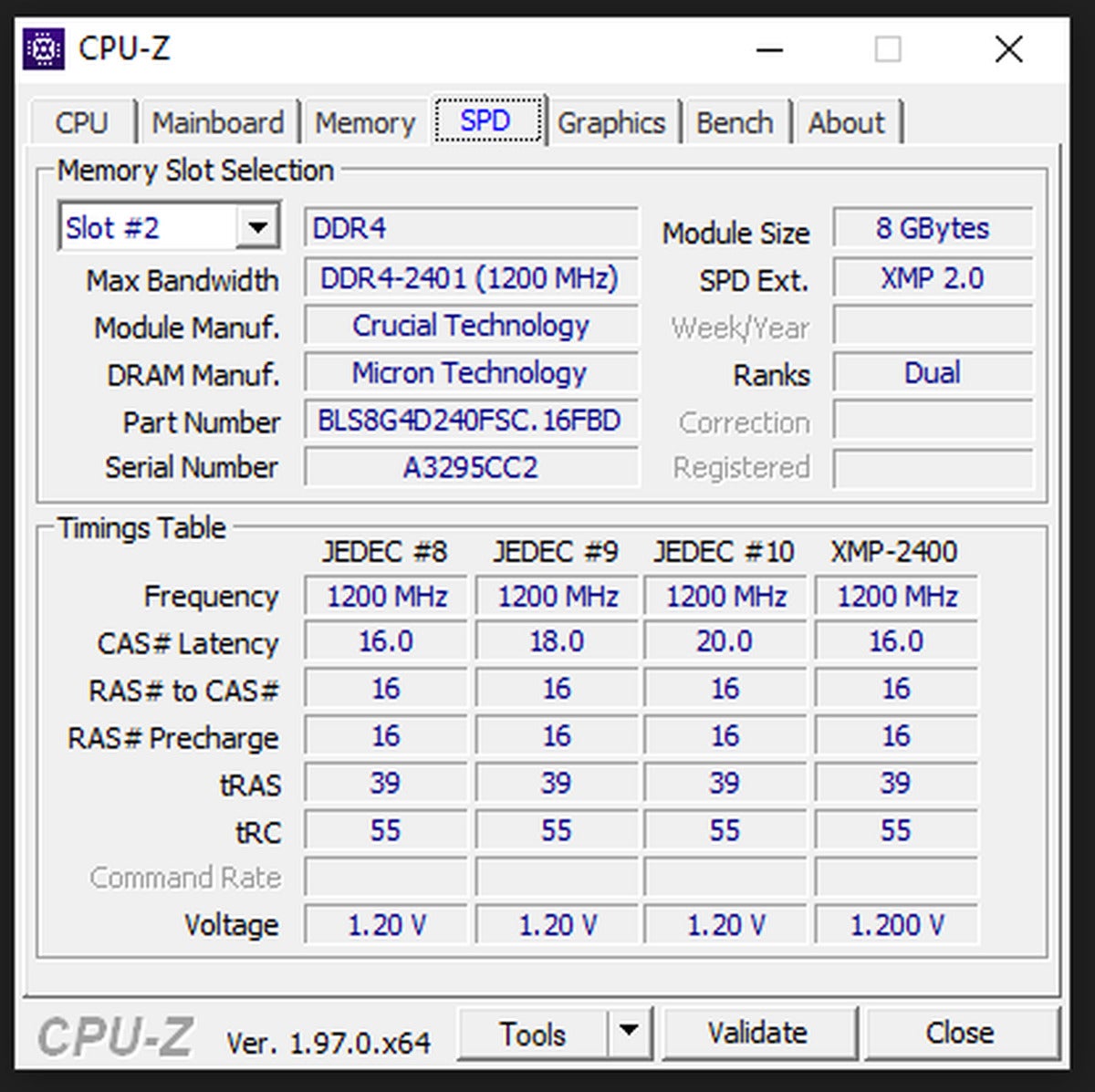 Kevin Casper/IDG
Kevin Casper/IDGIn CPU-Z, you’ll want to use the “Memory” and “SPD” tabs to see information about your RAM. Memory will show you memory type and current frequency information. The SPD tab, which stands for “serial presence detect,” provides information related to the RAM modules themselves including the manufacturer and part number information.
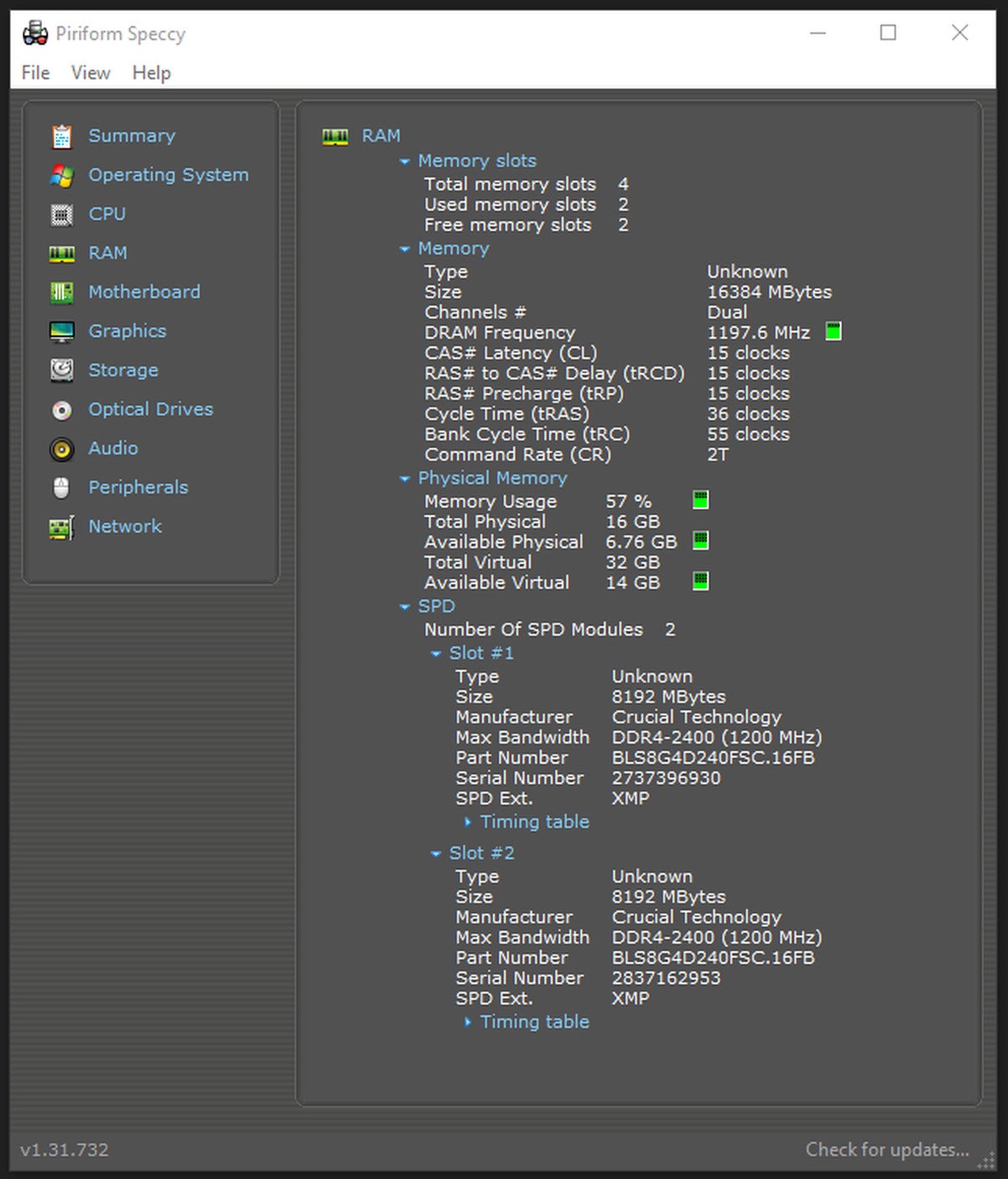 Kevin Casper/IDG
Kevin Casper/IDGIn Speccy, you’ll want to go to the “RAM” view from the left menu. In there, you should find virtually all of the RAM and memory information you’d need. You may need to expand the “SPD” drop-down in order to get more specific information about the RAM depending on what you’re trying to find.
In Linux
You can find virtually all of the information shown above via your Linux terminal by using the following command:
- sudo dmidecode —type memory
This should provide a sorted list of information about your memory devices, aka your RAM, including size, types, and manufacturer information.
Physical RAM module
Most consumer RAM modules will come with a label to identify the type of RAM it is. Typically, these labels will either be a sticker applied directly to the stick of RAM, engraved onto the fancy heat spreader on higher-performance modules, or may be printed directly onto the circuit board. In these cases, you’ll typically find the part number, which you can then look up with your favorite search engine to figure out the rest of the specs. If you can’t locate a label or identifier anywhere, then it may be prudent to use one of the methods described above instead.
These options should help you figure out what RAM your PC is using. If you’re looking to upgrade, be sure that you’re getting the same type and form factor of RAM, because you can’t directly swap out DDR3 for DDR4 RAM without having to also replace your motherboard. For more information on upgrading RAM, see our guide on How to install new memory in your PC.
Note: When you purchase something after clicking links in our articles, we may earn a small commission. Read our affiliate link policy for more details.
Kevin is a tech professional who is adept with public speaking, duct tape, and playing an orc in any game he can.
Market
.style-4_big #ccpw-ticker-7653 .coin-container:after{border-color:rgba(0,0,0,.18)}.ccpw-ticker-cont ul#ccpw-ticker-7653 li{background-color:#fff}.ccpw-ticker-cont ul#ccpw-ticker-7653 li .ticker-name,.ccpw-ticker-cont ul#ccpw-ticker-7653 li .ticker-symbol,.ccpw-ticker-cont ul#ccpw-ticker-7653 li .live-pricing,.ccpw-ticker-cont ul#ccpw-ticker-7653 li .ticker-price{color:#000}
Forget video, Zoom wants to fuse Slack and Teams


AMD Radeon Software can overclock your Ryzen CPU now, too


How to tell what kind of RAM you have


Bitcoin (BTC) Struggles to Maintain Support After Weekly Fall


Ark Invest Fund to Allow Participation in Canadian Bitcoin ETF


Bitcoin hits $45K ahead of July inflation report, but one fractal hints at looming correction
Identity management org Sailpoint unveils no-code tool


Minority communities are investing in crypto to escape financial discrimination


Crypto Crime Falls in China, Surges in Hong Kong, Reports Reveal


Coinbase beats earnings estimates as analysts say regulation will ‘stifle’ innovation